Application Programming Interfaces (APIs) have become the silent backbone of our digital world. From your banking app to your connected thermostat, APIs orchestrate an invisible symphony of data exchanges. Yet, this ubiquity conceals a concerning reality: in 2023, the average cost of a data breach related to an API flaw exceeded $3.8 million. In the case of ransomware, attacks increased by 150% between 2019 and 2022, according to The Harvard Business Review.
Paradoxically, while organizations invest heavily in traditional cybersecurity, APIs often remain in a blind spot. This article delves into what has become one of the major challenges of modern cybersecurity, exploring critical vulnerabilities, emerging solutions, and future prospects.

I. State of Play: The API Threat Landscape in 2024
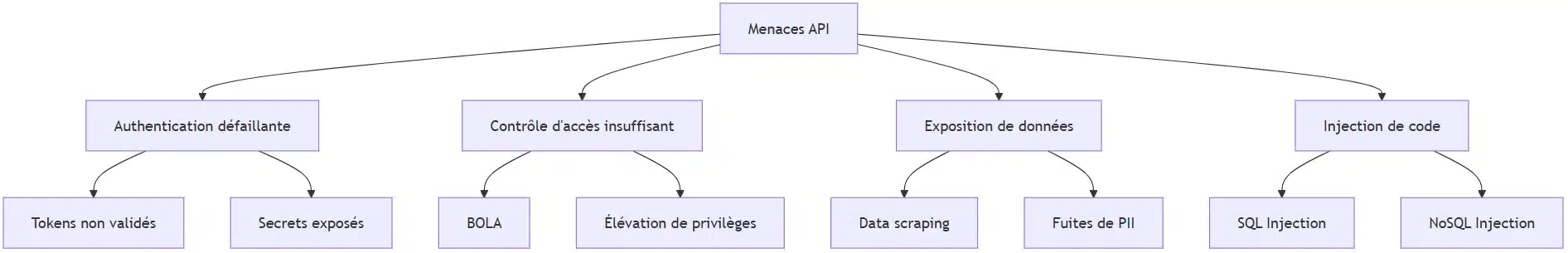
The year 2024 marks a turning point in the API threat landscape, with four categories of vulnerabilities being particularly concerning. Failed authentication is at the forefront, accounting for 46% of critical incidents reported. The most common scenario involves JWT tokens, a type of digital “ID card” used to transmit information, which are misconfigured or not verified, allowing attackers to forge legitimate identities. More worryingly, the frequency of API secret leaks in public repositories continues to rise.
The BOLA (Broken Object Level Authorization) vulnerability remains a major threat. With a simple modification of identifiers in requests, attackers can access other users’ resources. A recent study reveals that 22% of public APIs tested exhibited this flaw.
nstances of excessive exposure of sensitive data are multiplying, with overly verbose APIs returning far more information than necessary. This overexposure facilitates large-scale automatic data extraction (“data scraping“) and significantly increases the attack surface.
The DataCorp incident perfectly illustrates these vulnerabilities: a test API left active in production allowed the extraction of 4.2 million customer records. More recently, a flaw in the API of a connected device manufacturer exposed the video streams of thousands of home cameras, highlighting the growing risks associated with IoT.
These incidents highlight a troubling reality: API security can no longer be an afterthought. The financial and reputational costs of breaches are increasing exponentially, pushing organizations to fundamentally rethink their approach to API security.
II. Critical Challenges of API Security
As an organization grows, APIs multiply and complicate security. For example, a fintech company can evolve from a simple payment API to a network of dozens of endpoints, third-party services, and internal microservices. Each endpoint becomes a potential vulnerability point: a mobile application exposes an average of 35 endpoints, and this number can reach thousands for multi-application organizations. Added to this is the complexity of internal communications between microservices, often orchestrated through 5 to 10 cascading API calls, making identity and anomaly management crucial.
The pressure of time-to-market also often leads developers to overlook security:
- 64% of developers deploy APIs with incomplete security testing.
- 42% do not have formal security review processes.
Technical debt worsens the situation, with “zombie APIs“, obsolete dependencies, or desynchronized documentation. More worryingly, 35% of APIs lack up-to-date documentation, 73% neglect rate limiting, and 81% ignore error management. These gaps increase the risk of errors and complicate audits.
To address these challenges, a systematic approach to API security, integrated from the design stage, is essential.
III. Solutions and Best Practices for Securing APIs

1. Security by Design
Integrating security from the design stage of APIs is now a necessity. This preventive approach involves rigorous measures, such as using OAuth 2.0 and OpenID Connect to manage access. These standards require strict implementation, with key rotation, token validation, and scope management. JWTs should favor RS256 for robust signing.
Intelligent rate limiting is also essential: beyond fixed quotas, adaptive solutions analyze behaviors to detect and block suspicious requests before they harm the system.
2. Advanced Monitoring
Continuous monitoring is indispensable for identifying anomalies. Modern systems analyze access patterns, geolocation of requests, and relationships between API calls. This level of behavioral analysis allows for the detection of complex threats that traditional approaches often miss.
Automated penetration testing complements this setup by simulating common attacks daily, anticipating potential vulnerabilities.
3. Governance and Standardization
Documentation via OpenAPI becomes strategic, facilitating security testing and interface validations. Rigorous API version management, combining evolution and stability, is also crucial.
Finally, continuous team training, blending theory and practical workshops, fosters a sustainable security culture. Security-focused code reviews strengthen the dissemination of best practices.
Securing APIs requires synergy between technology, processes, and training to respond to evolving threats while remaining agile.

IV. Future Prospects for API Security
Among emerging trends, Zero Trust architecture is redefining API security by eliminating any implicit trust, internal or external. Each request must prove its legitimacy, an essential strategy as network boundaries fade.
The API Security Mesh is another key innovation. Rather than centralizing controls at the gateway level, this approach distributes defenses within services, creating a secure and adaptable mesh.
Artificial intelligence is revolutionizing threat detection. With machine learning, systems identify subtle attack patterns and even predict malicious behavior before it occurs, offering unmatched proactive protection.
In the future, developers must incorporate best practices from the design stage using suitable tools and adopting defensive programming. Anticipating malicious uses becomes a key skill.
Architects must rethink their systems by integrating Zero Trust and Security Mesh principles, enhancing resilience and quickly isolating threats.
CISOs must reconcile security and agility by adopting flexible, risk-based governance while continuously training teams. Investing in these approaches ensures a better defense against increasingly sophisticated threats.
Conclusion
API security is at a crossroads. Faced with sophisticated threats, only organizations that cultivate a holistic and shared approach to security will succeed. Adopting paradigms like Zero Trust while respecting the fundamentals remains essential. Securing APIs is an ongoing effort, where vigilance and adaptation remain our best assets.










