What is a Markov Chain?

A model is said to possess the Markov property if its state at time T depends solely on its state at time T-1. If we observe the states in which the model exists at each moment, we have what is known as an observable Markov model. Otherwise, it is referred to as a hidden Markov […]
Python with Google Colab: getting started with a remote team project

Google Colab is an online Jupyter notebook service that enables you to write and execute Python code directly from your web browser. Accessible for free with a Google account, Colab is perfect for data analysis and data science with Python, thanks to its code cells and text blocks in Markdown syntax, allowing you to structure […]
Figma: What is it? Why is everyone talking about it?

Figma is a cloud-based collaborative interface design tool. It enables you to create, prototype, and share designs in real-time without needing to install software or write any code. Discover what contributed to its rapid success! There was a time when designing a user interface required not just technical skills but also cumbersome, complex tools often […]
Data Modeling: What is it? How to use it?
Data Modeling is a frequently underestimated yet crucial step for the success of any data project. Discover what data modeling involves, the major types of models, and the best tools to use! Collecting data is one thing, but the most important part is understanding it. However, raw data is often as valuable as it is […]
Palantir: the power of data… or data in the service of power?

Palantir is a technology company specializing in the advanced analysis of big data. Originating within the sphere of American intelligence, it is now employed by militaries and industries alike. Discover its flagship tools, its role in the new era of generative AI, as well as the controversies it incites! Data is a buzzword that everyone […]
No Code Application: the power to create in everyone’s hands

No Code applications are a revolutionary approach to designing digital tools without writing a single line of code, thanks to AI and visual platforms. This method democratizes app creation for everyone, from freelancers to large corporations. Discover everything you need to know! Historically, creating an application was akin to a daunting battle: learning to code, […]
One-Hot Encoding: What is it? How to use it?
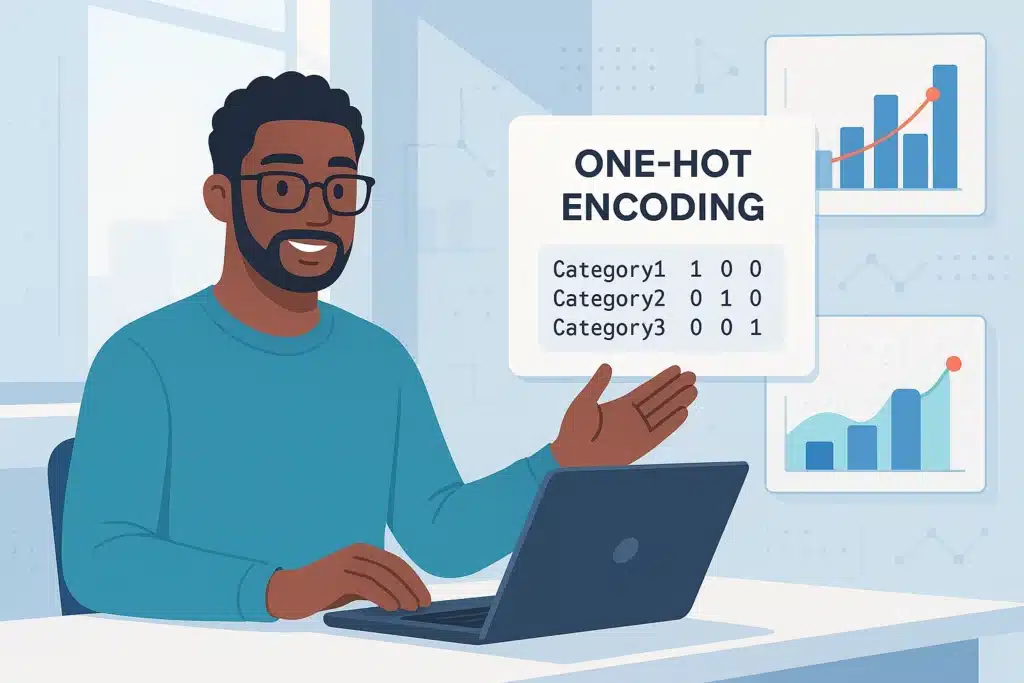
One-Hot Encoding is a technique that allows categorical data to be converted into numerical vectors that can be utilized by machine learning models. Discover everything you need to know about this method! Machine learning algorithms are incredible computational tools, but they have a major limitation: they do not comprehend text. For these systems, words like […]
SAP HCM: the HR module to manage your talents and processes

SAP HCM is the historic human resources management module integrated with SAP ERP. Covering everything from personnel administration to payroll, as well as time management and training, it structures the HR processes of thousands of companies globally. Explore its full array of features and the essential skills needed to master its use! Talent management, automation […]
Open SAP: Training in SAP has never been easier

Open SAP is a free online course platform launched by SAP to democratize access to its technologies. It attracted thousands of learners worldwide… before being replaced in 2024 by SAP Learning. Discover why it made such an impact and how to continue learning effectively! Learning SAP is often seen as a daunting task: expensive courses, […]
Stochastic Modeling: Principles, Methods, and Applications

What is Stochastic Modeling? Stochastic modeling involves a mathematical technique that depicts the progression of a system subjected to random influences on certain components. Instead of providing a single outcome, the model assigns a probability distribution to potential outcomes, enabling the simulation of various scenarios and measuring uncertainty. This method differs from deterministic models, which […]
Minimum Viable Product (MVP): What is it?

The Minimum Viable Product is a method that involves creating a simplified yet functional version of a product to quickly test an idea in the market. Discover why it has become an essential strategy for startups! Building a digital product often feels like a race against time. Too slow, and a competitor overtakes you. Too […]
Free no-code tools: the best ones to test
Can you create an app, a website, or an automation tool without knowing how to code? Thanks to free no-code platforms, now you can. In this article, discover what no-code is, how to select the right platform, and most importantly, which free tools to try today to bring your ideas to life. What is no-code? […]


