Our daily lives, work, and leisure activities now heavily depend on digital services. Over the past two years, however, all major reports (Verizon, ENISA, CrowdStrike, Unit 42…) highlight a consistent trend: attacks are increasing in frequency, power, and sophistication.
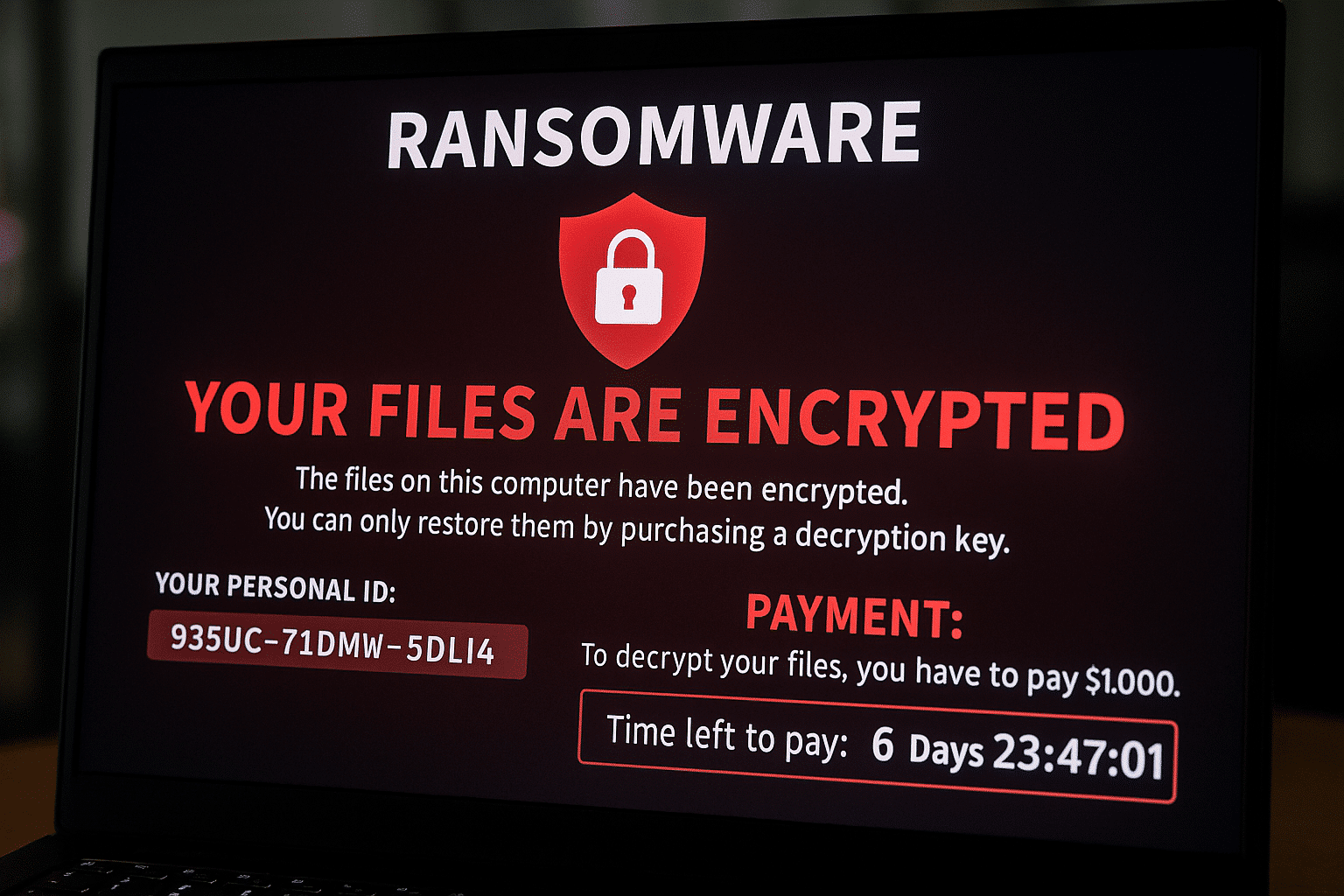
1. Ransomware: Pay or lose your data?
Ransomware encrypts your files and then demands payment to make them accessible again. In 2024, these malicious programs have once more targeted hospitals, SMEs, and communities. What’s new? The model, now “as-a-Service”, has become more sophisticated: affiliate programs and help-desks for victims. Attackers introduce a “double extortion” scheme. They initially copy data and threaten to publish it if the ransom isn’t paid. Even backups aren’t sufficient anymore; preventing intrusion beforehand is critical.
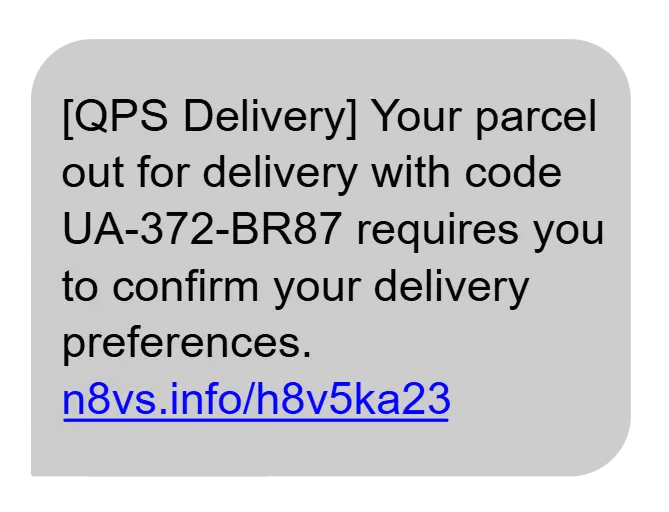
2. Phishing & Social Engineering
Phishing acts as a form of digital bait, where a fake email or SMS prompts you to click, allowing the mimicked login page to collect your credentials. By 2025, these messages can even mimic your writing style thanks to artificial intelligence. A variant, “Business Email Compromise” fraud, uses a fake “CEO” email to request urgent transfers. It’s essential to check the sender’s address, analyze links before clicking, and if unsure, directly call the person supposedly making the request.
3. Artificial Intelligence… aiding both sides
AI is a versatile tool, aiding defenders to spot anomalies, but also supporting attackers. It’s employed to:
- Create personalized phishing emails;
- Generate malware that continually changes its appearance;
- Assist a botnet (a network of compromised computers) in targeting specific individuals.
The flip side is that AI models themselves can be compromised (training data poisoning, chatbot hijacking). If you utilize AI, treat it as a critical asset by logging its usage, monitoring API key access, etc.
4. Cloud Misconfigurations
Online services (AWS, Azure, Google Cloud platform…) simplify life, but a misconfiguration can expose millions of records. At the end of 2023, Toyota unintentionally left vehicle location data public. This advice applies to companies of all sizes—enable two-factor authentication on administrative consoles, regularly audit account permissions, encrypt sensitive data, and monitor access logs.

A poorly secured surveillance camera, thermostat, or robotic arm can become a hacker’s entry point. At best, the device joins a botnet, a network of compromised devices used for massive attacks. At worst, the attacker penetrates the industrial network, disrupting production. Best practices include changing default passwords, isolating devices on a subnet, and updating promptly.

6. Software Supply Chain
Rather than directly targeting their victims, some hackers infiltrate a software provider, insert malicious code into a legitimate update, and then let the software compromise all customers. The SolarWinds incident (in 2020) and the tainted update of the 3CX software (in 2023) illustrate this threat. Companies are adopting the SBOM (Software Bill of Materials), an “inventory” of components, to better track fixes.

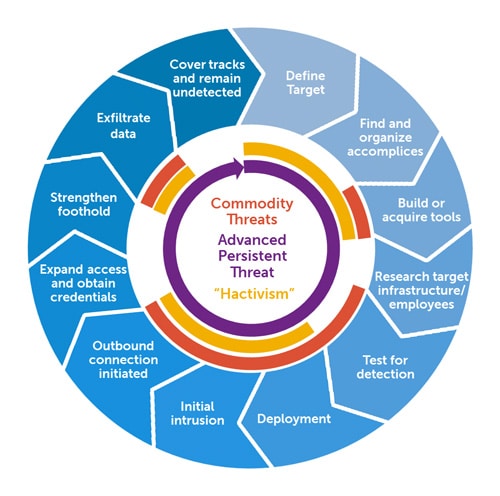
7. APT Groups: When geopolitics comes into play
APT (Advanced Persistent Threat) groups are often linked to states. They have the resources and time to steal intellectual property or sabotage critical infrastructure. International tensions (the war in Ukraine, economic rivalries) fuel their activities. For companies in sensitive sectors, strategic monitoring (indicators of compromise, best network segmentation practices) becomes imperative.
8. DDoS Attacks
A DDoS attack involves overwhelming a server with excessive requests to incapacitate it. The latest technique, the HTTP/2 Rapid Reset attack, has achieved peaks of over 200 million requests per second. Attackers use these methods for extortion, to protest against an organization, or to obscure an ongoing hack. Protection measures include upstream filtering systems and backup solutions like mirror sites or stand-by pages.

9. Data Leaks and Extortion
As soon as a customer database appears on the dark web, a company suffers financial and reputational damage. Leaks can result from hacking (data breach) or human error (data leak). Recently, some groups have started stealing information and demanding a ransom without even encrypting systems. To mitigate damage, encrypt sensitive data, restrict access to the bare minimum, and monitor any unusual exfiltration activities.
10. Zero-Day Vulnerabilities and Express Patching
A zero-day flaw is unknown to the vendor when exploited by an attacker. According to Google, in 2023, nearly a hundred have been observed in the wild. Even after a patch is released, attackers quickly use it before everyone updates. This underscores the importance of patch management! Prioritize patches for systems exposed to the Internet (VPN, messaging, web servers) and, in the meantime, employ filtering or segmentation.
What is OWASP preparing for its Top 10?
OWASP (Open Web Application Security Project) publishes a list of the top ten web security vulnerabilities every four years. In 2021, the leading themes were unauthorized access, software integrity, and insecure design. For 2025, focus shifts to three areas: software supply chain, API and microservices security, and authentication methods. While SQL or XSS injections remain threats, modern frameworks complicate their exploitation. OWASP now advocates DevSecOps, which integrates security from the development stage.
In conclusion
In 2025, cyberattacks are faster, more extensive, and leverage artificial intelligence. However, most incidents share a commonality: a basic human or technical flaw left unaddressed for too long. Protecting against them isn’t solely about colossal budgets; it fundamentally revolves around basic hygiene: keeping systems updated, scrutinizing suspicious emails, managing access strictly, maintaining offline backups, and assigning responsible parties. Cultivating these practices is more effective than a state-of-the-art firewall left unsupervised. Ultimately, cybersecurity is less about gadgets and more about behavior.

Bibliography
- Verizon – “Data Breach Investigations Report 2024”
https://www.verizon.com/business/resources/Tb2/infographics/2024-dbir-finance-snapshot.pdf
- ENISA – “Threat Landscape 2023”
https://www.enisa.europa.eu/sites/default/files/publications/ENISA%20Threat%20Landscape%202023.pdf
- IBM – “Cloud security evolution: Years of progress and challenges”
https://www.ibm.com/think/insights/cloud-security-evolution-progress-and-challenges
- Palo Alto Networks – “Unit 42 Threat Intelligence Reports”
https://unit42.paloaltonetworks.com/
- Google Threat Analysis Group – “A Review of 0-days Exploited In-The-Wild in 2023”
https://blog.google/technology/safety-security/a-review-of-zero-day-in-the-wild-exploits-in-2023
- Cloudflare – “ HTTP/2 Zero-Day vulnerability results in record-breaking DDoS attacks”
https://blog.cloudflare.com/zero-day-rapid-reset-http2-record-breaking-ddos-attack
- Google Cloud – “ A review of zero-day in-the-wild exploits in 2023″
https://blog.google/technology/safety-security/a-review-of-zero-day-in-the-wild-exploits-in-2023
- OWASP – “ OWASP Top Ten (2021)”
https://owasp.org/www-project-top-ten/
- OWASP – “API Security Top 10 (2023)”