A MAC (Media Access Control) address is a unique identifier assigned to every network interface of a device. It plays a pivotal role in facilitating communication within local networks. MAC addresses are hard-coded into the network hardware during manufacture, serving a vital function in the identification of devices within a network.
In addition to their crucial role in identification and communication, MAC addresses are instrumental in network security. They enable the implementation of filtering mechanisms to allow only authorized devices to connect to a network, thus providing an additional security measure against unauthorized access.
What is a MAC Addresses?
Their Structure
MAC addresses are distinct identifiers comprising 48 bits, or 6 bytes, assigned to the network interfaces of devices. These identifiers are commonly expressed in hexadecimal notation for greater conciseness and readability. A typical MAC address is formatted as follows: 00:1A:2B:3C:4D:5E, where each pair of hexadecimal digits (00, 1A, 2B, etc.) corresponds to a byte, or 8 bits, of the MAC address.
| 8 bits | 8 bits | 8 bits | 8 bits | 8 bits | 8 bits |
|---|---|---|---|---|---|
| 00 | 1A | 2B | 3C | 4D | 5E |
| Manufacturer's unique identifier | Device's unique identifier | ||||
The structure of MAC addresses is bifurcated into 2 components:
- Organizationally Unique Identifier (OUI): The initial 24 bits of a MAC address are earmarked for identifying the network card’s or interface’s manufacturer. This unique identifier is allocated by the IEEE (Institute of Electrical and Electronics Engineers), ensuring that each manufacturer possesses a distinct range of addresses.
- Device-specific identifier: The remaining 24 bits are utilized by the manufacturer to bestow a unique identifier upon each product. This guarantees the global uniqueness of each MAC address.
Due to its succinctness and clarity, hexadecimal notation is employed for representing MAC addresses. In this format, each digit signifies four bits (half a byte), allowing the condensation of the 48 bits into 12 hexadecimal characters. For instance, the binary notation for the previously mentioned MAC address would be denoted as: 00000000 00011010 00101011 00111100 01001101 01011110, which is significantly less intuitive.
MAC Address versus IP Address
Grasping the distinction between a MAC address and an IP address is crucial, as they fulfill complementary functions in network communication.
- MAC Address: A MAC address is a permanent, exclusive identifier allocated to a network interface. It functions at the data link layer (layer 2) of the OSI model, facilitating communication within a local network.
- IP Address: An IP address is a bestowed identifier enabling a device’s location and communication on a network. Contrary to the permanent nature of a MAC address, an IP address can fluctuate based on network settings and the device’s connectivity. It operates at the network layer (layer 3) of the OSI model.

Simply put, while the MAC address identifies a device’s physical network interface, the IP address denotes the device’s logical presence on a network.
How to Locate Your MAC Address?
The method to locate your MAC address varies depending on your operating system, commonly referred to as the “physical address.”
1. Windows
In a command prompt window cmd, enter ipconfig /all. This action will display an outcome akin to the following:
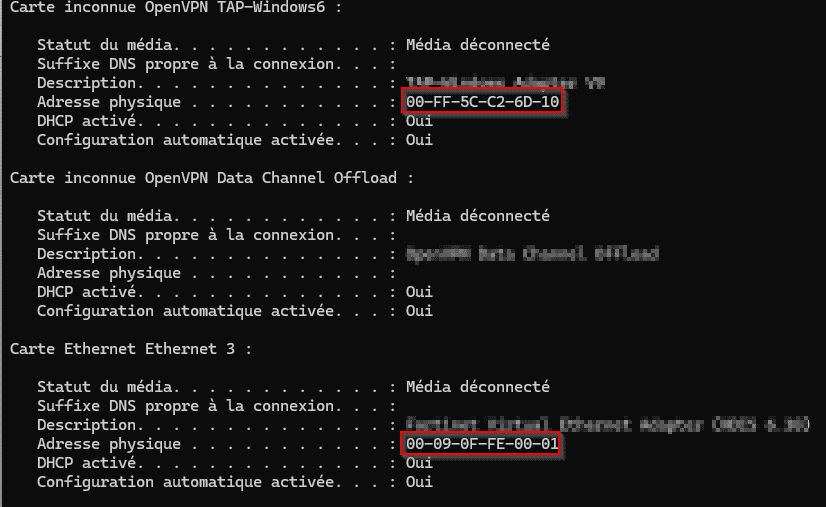
Should you have numerous network adapters, then multiple outcomes, each revealing a distinct MAC address, will be shown.
If the graphical interface is your preference, this information is accessible in your network device’s properties by navigating through Settings followed by Network and Internet.

2. Linux
Via a terminal, employing the ip addr show command, as exemplified in the screenshot below:

3. Other OS
Regardless of the operating system—be it Macintosh, Android, or iOS—the procedure to find your MAC address remains largely analogous. This information can be located in the settings of the device in question.
Security and Privacy
Given their unique and permanent characteristics, MAC addresses open the door to potential tracking and surveillance hazards. To bolster security, many devices and operating systems provide options to conceal or modify the MAC address.
Network administrators frequently employ MAC filtering as a means of permitting only preselected devices to connect to the network, thereby introducing a barrier against unauthorized access. Powerfully managing and securing these addresses is imperative for sustaining network integrity and confidentiality.
Conclusion
A profound comprehension and managerial acumen of MAC addresses are indispensable for promoting efficacious and secure communication in local networks. By acquainting oneself with their structure, function, and the techniques for discovering them, one can enhance the security of their devices and refine their network’s performance.










