Amazon Elastic Kubernetes Service (EKS) is a service offered by AWS that enables you to deploy, manage and scale containerized applications using Kubernetes technology, the powerful and widely adopted open-source container orchestrator.
Defining a Kubernetes cluster
Before going into more detail on how Amazon EKS works, let’s take a look at what a Kubernetes cluster is. It’s a container management infrastructure that brings together a set of virtual or physical machines (called nodes) to run and orchestrate containerized applications. Kubernetes (often abbreviated K8S) provides a powerful and robust framework for deploying, scaling and managing containers.
Anatomy of an EKS cluster
An Amazon EKS cluster is made up of several interconnected elements that work together to run, manage and orchestrate your containerized applications. Understanding the architecture of an EKS cluster is essential to ensure its effective use and management.
The essential components of an EKS cluster
The table below shows the various components of an EKS cluster.
 |
Worker Nodes | These are the machines where containers run. They are EC2 instances launched in the EKS cluster. Worker nodes are managed by the EKS control plane service and can be fully managed as needed (start or stop, as well as scaling). |
|---|---|---|
 |
Control Plane | This is the central part of the architecture of an EKS cluster. It manages the entire system, including pod scheduling, workload distribution, update management, and cluster state monitoring. Managed entirely by AWS, you don't have to worry about it directly. |
 |
API Server | The API server is an essential component of the Control Plane. It exposes the programming interface that allows users or tools to communicate with the EKS cluster. |
 |
Load Balancing | EKS clusters integrate load balancing services, such as ELB or NLB. These services intelligently distribute traffic between nodes running containers. |
 |
Amazon VPC (Virtual Private Cloud) | Amazon VPC is an AWS virtual network service that isolates and secures resources in an EKS cluster. Each EKS cluster is associated with one or more subnets, providing network isolation and logical segmentation for cluster resources. |
 |
IAM (Identity and Access Management) | IAM is the AWS identity management service. It allows for granular permissions management on roles and user permissions, restricting access to sensitive cluster resources. |
EKS cluster architecture
Now that we’ve defined the fundamental elements of an EKS cluster, let’s see how it’s all organized.
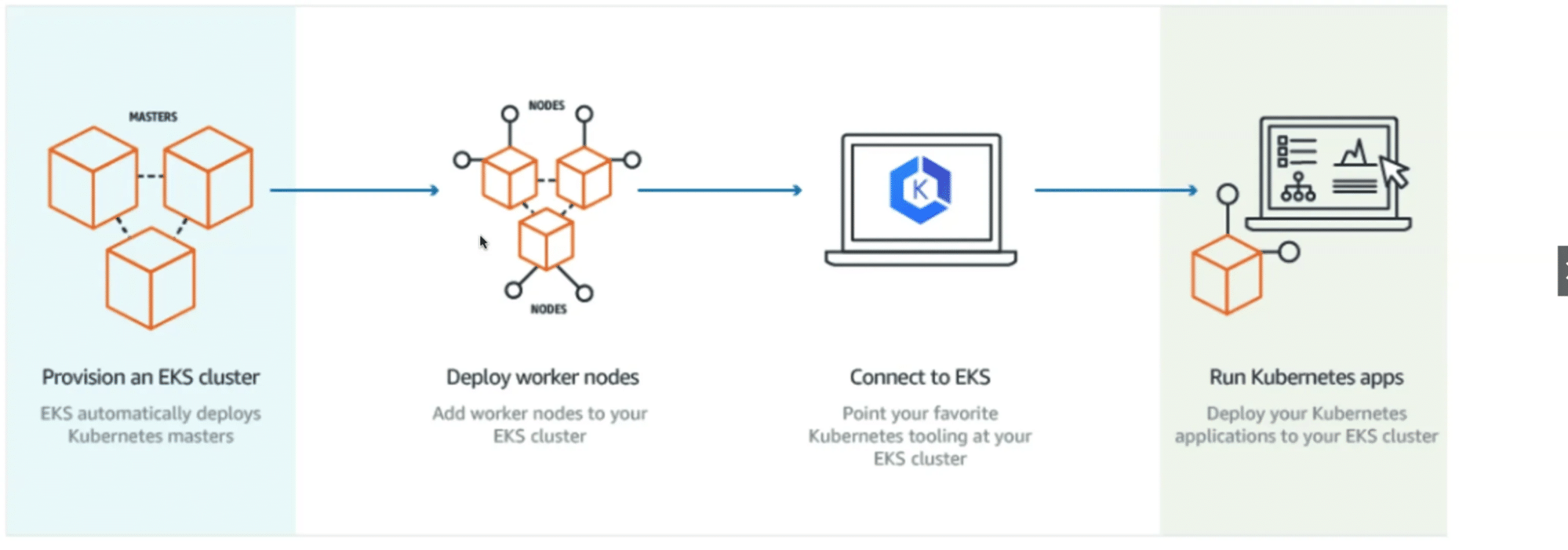
The diagram below illustrates the interconnections between the various elements:
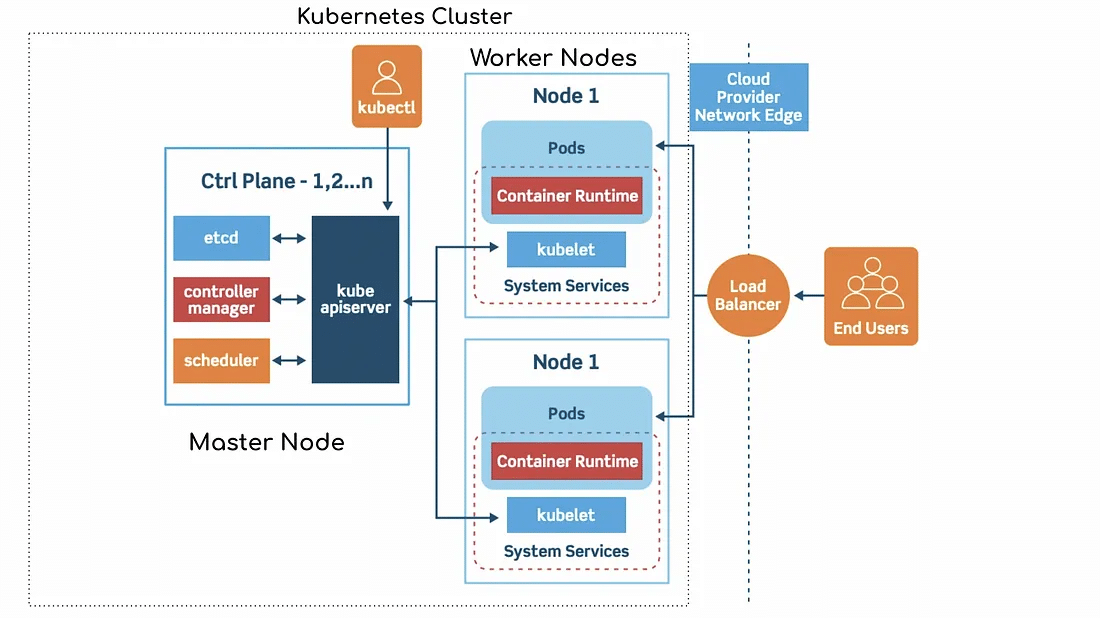
- The first step is to provision your EKS cluster. The master node will be deployed automatically by EKS. This node will therefore contain the appropriate control center to enable you to manage your resources.
- The next step is to deploy your worker nodes. These are nothing more or less than a group of EC2 instances.
- To properly deploy your workloads in your work nodes, you’ll need to connect them to EKS.
- To do this, you’ll mainly be using Kubectl (CLI), a widely-used tool for creating and deploying your workloads.
- Now your containerized applications deployed in your clusters are up and running, ready to be run inside the cluster or exposed to the outside world.
How do you secure EKS clusters?
Every EKS cluster needs to be secure, to protect applications and data from potential threats. Amazon EKS offers a range of tools and best practices to help you protect your clusters.
 |
Role-Based Access Control (RBAC) | EKS uses Kubernetes' RBAC to manage user and application permissions. With RBAC, you can define roles, groups, and authentication bindings to control access to EKS cluster resources. |
|---|---|---|
 |
Network Access Control (NAC) Policies | EKS NAC allows control over network communications between pods, services, and worker nodes in a cluster. You can define fine-grained security rules based on IP addresses, ports, and protocols to restrict data flows and prevent unauthorized access. |
 |
Data Encryption | EKS supports data encryption. You can use SSL/TLS certificates to secure communications between cluster components. To ensure data stored confidentiality, AWS services like EBS and S3 can be utilized. |
 |
Identity and Access Management (IAM) | As mentioned earlier, IAM allows you to manage identities and resource access for your EKS cluster by defining roles with specific permissions. |
 |
Security Updates and Patches | EKS provides regular updates and patches. It's essential to keep your EKS cluster up to date by applying recommended updates to benefit from the latest security enhancements and vulnerability patches. |
 |
Monitoring and Audit | Like most AWS services, EKS offers built-in monitoring and audit features to help you detect suspicious activities and identify potential security issues. Services like CloudWatch or CloudTrail allow you to collect activity logs and take corrective actions. |
Conclusion
The Amazon Elastic Kubernetes Service (EKS) solution offers a powerful, scalable platform for deploying and managing containerized applications. In this article, we explore the different aspects of an EKS cluster.
It’s essential to follow best practices and security recommendations to ensure the protection of your EKS cluster.
By keeping your cluster up-to-date, applying security patches, controlling access and actively monitoring activity, you can enhance the security of your EKS cluster and ensure that your applications run smoothly.










