What is Amazon IAM?
AWS Identity and Access Management (IAM) is AWS’s identity and access management service. When you use any Amazon AWS service, whether it’s web hosting, Kubernetes clusters, virtual machines, etc., you will automatically go through an authentication phase, during which the IAM service will grant you varying levels of access based on the permissions that have been assigned to you.
The different IAM entities
IAM has several entities that allow you to fine-tune access to different resources:
| Entity | Description | When to Use |
|---|---|---|
User |
Every person needing access to your AWS resources should have a user account. Permissions are then defined through access policies. | Grant specific access to individuals for certain tasks. |
Groups |
This is a set of users with common permissions. Users can be added or removed as needed. | Grant common permissions to a group of user accounts. |
Roles |
Roles are used to temporarily grant permissions to users or AWS resources. | Use roles when you need to temporarily grant permissions to users or resources. |
Access Policy |
A Json document defining permissions for one or more IAM entities. These policies determine the actions users can perform on resources and the conditions under which these actions can be performed. | Use access policies to define granular permissions for each IAM entity in your AWS account. |
Credentials Report |
A report providing information on different authentications and authorizations in your IAM account. | Audit and monitor user access and detect security anomalies. |
Identity Provider |
A third-party service to provide authentication to your resources via other providers (Google, Facebook, Cognito, etc.) | Authenticate through a third-party service rather than AWS credentials. |
How does IAM work?
AWS IAM is fully compatible with most AWS compute, container, storage, database and other cloud offerings. However, AWS IAM is not fully compatible with all platform offerings, so it’s best to check compatibility before implementing the service.
The IAM infrastructure is illustrated in the following diagram:
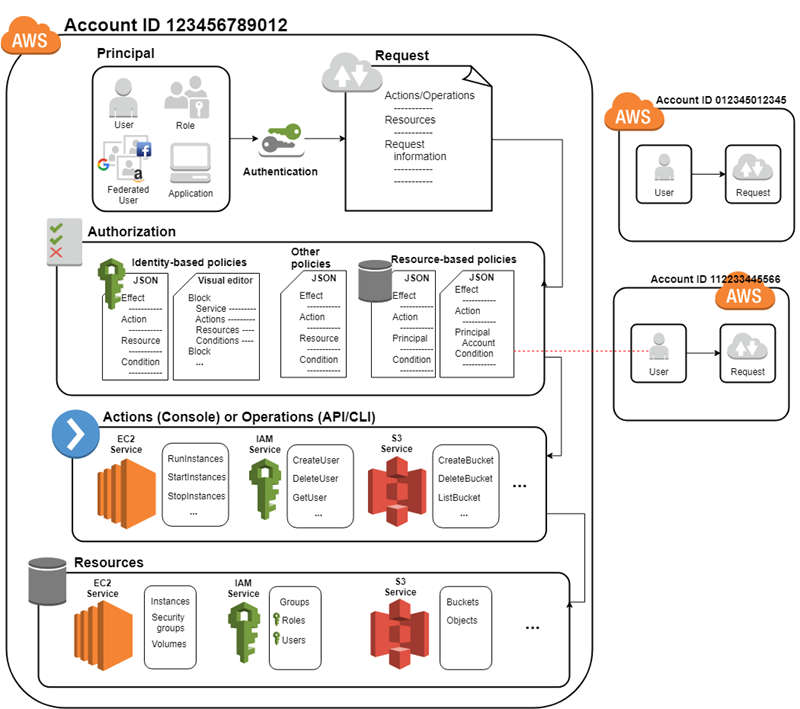
Explanation: A principal (human user or application making a request to use AWS resources) uses its credentials to authenticate itself. A request is made to grant access to the principal. Access is granted by means of an authorization request. Once authorized, the principal is able to perform actions or operations on your AWS account.
A few best practices
✅ Never use the root user to perform routine tasks.
✅Human users must use temporary credentials to access AWS resources. You can use an identity provider for these users to assign them a role that will provide temporary credentials.
✅Use multi-factor authentication (MFA) for users and roles.
✅Provide regular access key rotation for uses requiring long-lasting credentials.
✅To grant the necessary permissions for a specific task, it is advisable to use minimal access policies based on the desired activity. IAM Access Analyzer will enable you to generate and audit these policies.
✅Regularly review users, accounts, roles, and security policies, and delete those that have become obsolete, or are unused.
Conclusion
In conclusion, IAM lets you manage identities and access to an AWS account. This service enables you to control resource access authorizations, audit resource use and manage security policies. In this way, your users can enjoy a high level of security, while benefiting from the flexibility and scalability offered by AWS.










