Network protocols are rules and standards that enable computers to communicate with each other and share data. These protocols are used in different types of networks, such as the local area network (LAN) and the wide area network (WAN), to ensure communication and collaboration between users.
But what are network protocols? Why are they important? What are the different types of network protocol? Answers to your questions in this article.
What is a network protocol?
Before delving into the details, it is important to understand what a network protocol is. A network protocol is a standard or set of rules that defines how computers communicate with each other.
Network protocols define the data formats, message types, authentication methods and access control methods that are used to ensure secure and reliable communication.
They are essential for communication between computers and thousands of different protocols have been developed over time.
What role do network protocols play in communication?
Network protocols are essential for communication between computers, as they enable standardised and efficient messages to be sent.
Without network protocols, computers would find it difficult to communicate consistently and reliably. They also guarantee the security and confidentiality of data.
There are different types of network protocol, each with its own characteristics and functions. For example, TCP (Transmission Control Protocol) is used to ensure reliable communication between computers, while UDP (User Datagram Protocol) is used for faster but less reliable communication.
In addition, network protocols are used in many fields, such as telecommunications, computing, industry and medicine. For example, DICOM (Digital Imaging and Communications in Medicine) is used for medical images, while VoIP (Voice over Internet Protocol) is used for voice communications over the Internet.
Network protocols are often detailed according to the OSI layer to which they belong.
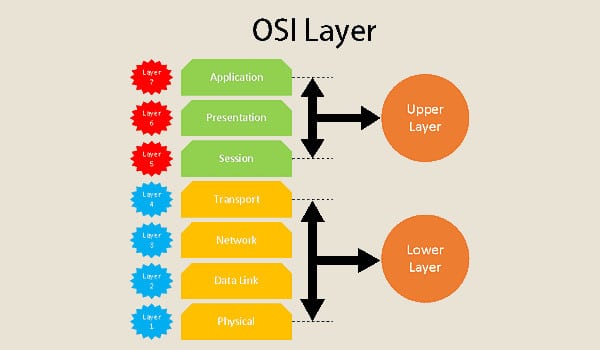
The layers of the OSI model
The OSI (Open Systems Interconnection) model is a representation of Internet working communications. Most network protocols are based on the OSI model. It contains 7 layers:
- The application layer: the human-computer interaction layer, which enables applications to access network services.
- The presentation layer: encodes and decodes data, ensuring that data can be used in different systems.
- The session layer: maintains connections and manages user sessions.
- The transport layer: manages protocol delivery (more on this in the next section).
- The network layer: routes data through suitable network resources.
- The data link layer: defines the format of the data on the network.
- The physical layer: defines the electrical, mechanical and optical characteristics. It acts as the interface between the network and the devices.
The different types of network protocols
Now that you know the 7 layers of the OSI model, it’s time to discover the different types of network protocols within the different layers.
Application layer protocols
Application layer protocols are protocols that allow programs to send information to each other in a structured and organised way. Application layer protocols are often used for web communication. The best-known application layer protocols include :
- HTTP: used for communication between browsers and web servers.
- FTP: used to transfer files between computers.
- SMTP: used for sending emails.
- POP3: used to retrieve emails.
- DNS: used to map host names to IP addresses.pplication
Transport layer protocols
Transport layer protocols are used for communication between computers. They ensure that data is sent and received without error and in the right order. Transport layer protocols are therefore very important for ensuring reliable communication. The most commonly used are :
- TCP (Transmission Control Protocol): used for reliable connections, where all data must be received in order. This service is reliable thanks to a sequenced acknowledgement.
- UDP: used for unreliable connections, where some data loss is acceptable.
- SCTP: used for reliable connections, but with better congestion management (avoiding bottlenecks) than TCP.
Network layer protocols
Network layer protocols are used for communication between networks. They enable data packets to be routed between the various networks that make up the Internet. The most commonly used network layer protocols are :
- IP (Internet Protocol): used for addressing and routing data packets.
- ICMP (Internet Control Message Protocol): used to manage errors and control messages.
Data link layer protocols
Data link layer protocols are used to control the flow of data over a communication channel. They ensure that data is sent and received without error by detecting and correcting packet transmission errors. The most commonly used data link layer protocols are :
- HDLC: used for communication between telecommunications equipment.
- PPP: used for communication between computers and telecommunications equipment.
- ATM: used for high-speed communication over telecommunications networks.
As for the presentation and session layer network protocols, two of them are worth knowing:
- RPC (session): used to request a service from a program located in another remote computer via a network, without having to understand the details of the network.
- LPP (presentation): used for simplified support of applications based on TCP/IP networks.
Network protocols in brief
Network protocols are essential rules and standards for communicating and sharing resources on a network. They enable efficient, standardised communication between connected devices and guarantee data security and confidentiality. By understanding the different types of network protocols and how they work, you can get the most out of using them.