Since 2018, Google has mandated the use of the HTTPS protocol as the security standard for websites. Most likely, your own site has adopted this safeguard. But should you feel completely secure? Not entirely. In truth, HTTPS connections can be vulnerable if they’re not properly configured. Ideally, the TLS protection they integrate should be robust. Here is more information…
The Internet became widely accessible to the public starting in 1995. The need to establish security standards quickly became apparent.
This concern actually emerged almost 10 years earlier when the Internet was mainly used by researchers and academics. In 1986, the U.S. government formed a standards organization—which later became autonomous—called the IETF or Internet Engineering Task Force.
In 1999, recognizing the growing importance of the Web and the security risks it posed, the IETF developed a security protocol named TLS – Transport Layer Security. Its purpose: to encrypt communications between two systems connected to the Internet. The most recent update (TLS 1.3) was released in 2018.
If you operate a website, it likely complies with the HTTPS standard, which is built on the SSL encryption standard. Can you assume your website is protected from every threat? Not necessarily.
HTTPS incorporates TLS
Initially, websites followed the HTTP standard, which lacked security. Data was transferred openly from a server to a browsing device, making it relatively easy for a hacker to intercept this information, including passwords and data submitted via a form.
To make the Web more secure, the company Netscape, which created the first popular web browser, developed an encryption protocol called SSL. Websites using this protection were identified by the HTTPS designation. By the late 2010s, Google deemed it essential and began penalizing HTTP sites in its search engine to encourage the shift to HTTPS.
What’s the difference between HTTPS and TLS? There’s essentially no difference. SSL and hence the HTTPS protocol incorporate the TLS algorithm.
In fact, HTTPS refers to implementing TLS encryption as an enhancement of the HTTP protocol. Hence, a website using HTTPS indeed relies on TLS encryption.
If you’ve read our earlier points, you might feel that HTTPS might not be sufficient in all situations. Why is that? Because some HTTPS implementations still depend on the original 1999 standard, namely TLS 1.0.
Therefore, it’s critical to ensure that an HTTPS TLS certificate specifies TLS 1.3. Why is this important?
What is a TLS certificate?
A website protected by HTTPS contains a TLS certificate. This certificate includes information about the domain owner and the server’s public key (derived from a confidential private key), which are crucial for authenticating the server. This kind of certificate is issued by a certification authority such as Let’s Encrypt, DigiCert, or GoDaddy, to a domain owner.
You can easily check any site’s certificate while browsing. Click the small icon in the address bar before a website’s address. This allows you to view the server’s TLS certificate—it’s sometimes called an “SSL certificate” due to confusion regarding the names of these protocols.

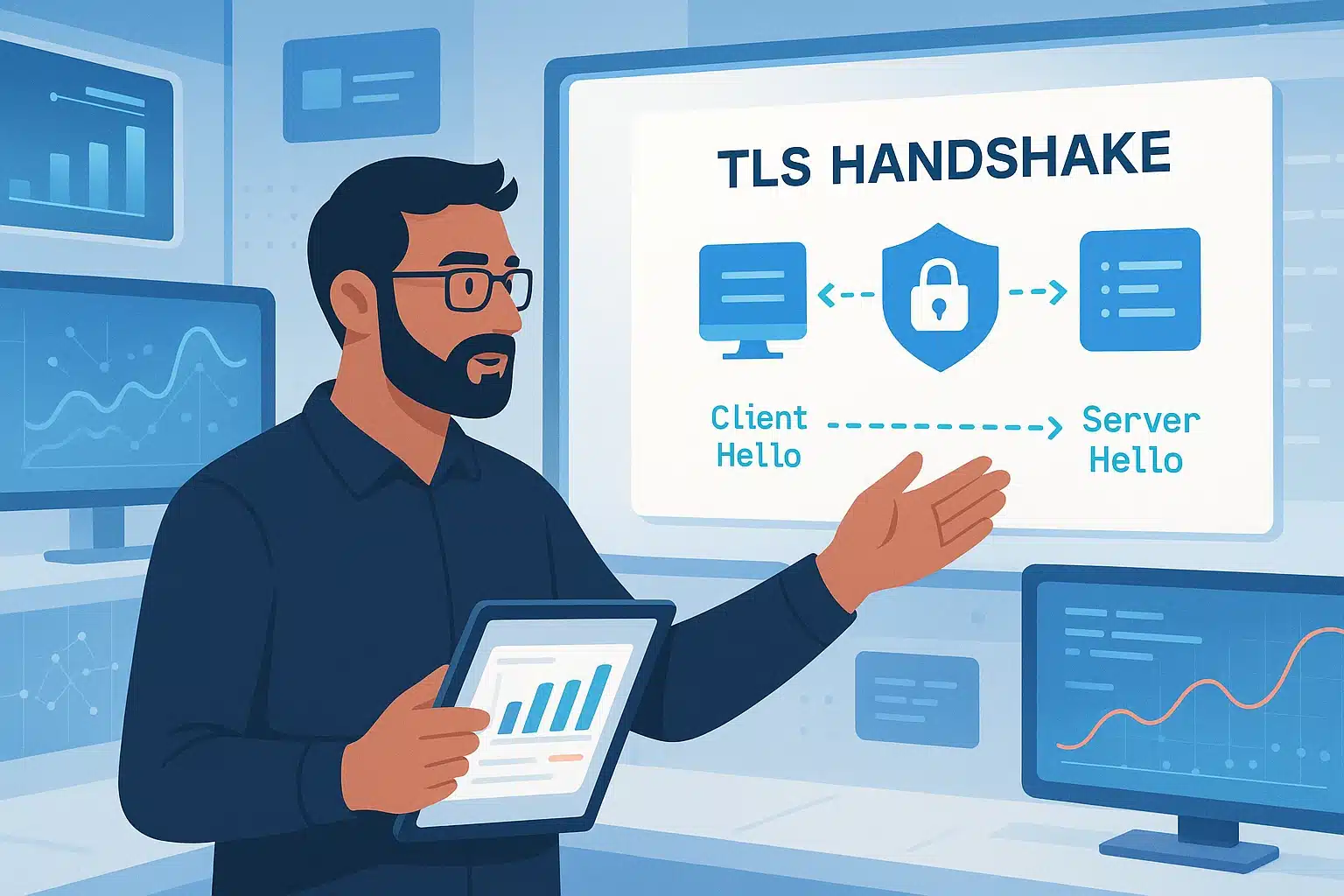
TLS handshake
To better understand how the certificate functions, let’s explore what happens when a connection via TLS is established between a computer and a web server.
When you enter or select a web address in your browser, a “TLS handshake” initiates between your computer or smartphone and the server hosting that website.
During this handshake, your computer and the server:
- Specify the version of TLS (TLS 1.0, 1.2, 1.3) being used.
- Agree on the encryption that will take place in the communication session between the user’s computer and the server. This encryption prevents data interception by third-parties.
- Authenticate the identity of the server via its TLS certificate, meaning the server must verify its identity to the requesting computer.
- Generate cryptographic keys that will manage the encryption of the data exchanged between both parties.
What has changed with TLS 1.3?
As we’ve mentioned, the initial handshake step involves establishing the version of TLS in use. However, versions TLS 1.0 and 1.1 are now considered outdated and insufficiently secure.
A series of attacks around 2010 highlighted vulnerabilities in the basic TLS protection. Notable attacks include:
- BEAST (2011).
- CRIME (2012) and BREACH (2013).
- Heartbleed (2014)
Major cloud platforms have long stopped supporting TLS 1.0. The suggested version is TLS 1.3. Why?
TLS 1.3 introduces the concept of Perfect Forward Secrecy (PFS). Each session has a temporary protection key. Even if a server’s private key is compromised, a hacker couldn’t reconstruct data from previous sessions—the decryption wouldn’t succeed.
The key takeaway: ensure TLS libraries are current, especially on e-commerce sites. Tools like Qualys SSL Labs can verify this for you.